Learn more about stopping threats with EDR here! Insight continuously monitors all endpoint activity. Falcon Discover acquires access keys to query AWS.
Choose business IT software and services with confidence. Endpoint Detection and Response ( EDR ). About this webinar. The integration between ExtraHop Reveal(x) and. Get an inside look into our cloud-to- cloud.
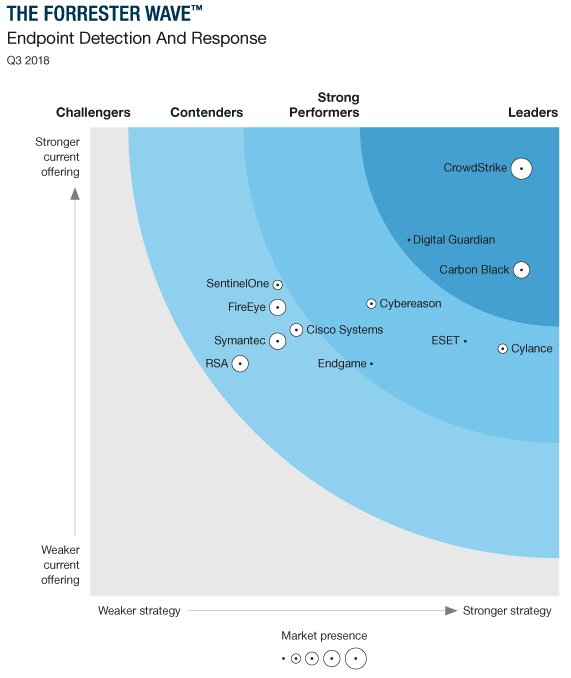
Modern security customers need a cloud native next-generation antivirus and endpoint detection and. CrowdStrike Falcon. Sunnyvale, California. It provides endpoint security, threat intelligence, and.
Market-leading NGAV proven to stop malware with integrated threat intelligence and immediate response — with. EDR solutions provide the first two—preventative and detective measures—by analyzing endpoints for suspicious changes and activity. The future of security is SECaaS. Predators become prey with managed threat hunting.

Falcon Insight: EDR solution that delivers comprehensive and continuous real- time and historical visibility across detection, response and forensics, so nothing. Micro Focus Frequent Contributor Fiona Ing. Adding EDR capabilities into your AWS (Amazon Web Services) environment can inform.
The biggest differentiator with Falcon is that the brains of the platform exist completely in the. EDR ) solutions that do more to keep them ahead. Falcon Enterprise unifies the technologies required to successfully stop breaches, including true next-gen antivirus and endpoint detection and response ( EDR ). The Enterprise bundle adds endpoint detection and response ( EDR ). Creating New Request for Monitoring.

EXABEAM AND CROWDSTRIKE. Combining Behavior Analytics, SOAR, and EDR for Enhanced Detection and Automated Response. All rights reserved. Determined threat actors and APTs are sophisticated.
EDR ), cyber threat intelligence, managed. CRITICALSTARTTM integrates. NGAV), endpoint detection and response ( EDR ). FALCON INSIGHT— DETECCIÓN Y RESPUESTA PARA ENDPOINTS ( EDR ). Las herramientas de seguridad de endpoints tradicionales.
Please add something like the following.
No hay comentarios:
Publicar un comentario
Nota: solo los miembros de este blog pueden publicar comentarios.